NO.20 Cluster: admission-cluster
Master node: master
Worker node: worker1
You can switch the cluster/configuration context using the following command:
[desk@cli] $ kubectl config use-context admission-cluster
Context:
A container image scanner is set up on the cluster, but it’s not yet fully integrated into the cluster’s configuration. When complete, the container image scanner shall scan for and reject the use of vulnerable images.
Task:
You have to complete the entire task on the cluster’s master node, where all services and files have been prepared and placed.
Given an incomplete configuration in directory /etc/Kubernetes/config and a functional container image scanner with HTTPS endpoint https://imagescanner.local:8181/image_policy:
1. Enable the necessary plugins to create an image policy
2. Validate the control configuration and change it to an implicit deny
3. Edit the configuration to point to the provided HTTPS endpoint correctly Finally, test if the configuration is working by trying to deploy the vulnerable resource /home/cert_masters/test-pod.yml Note: You can find the container image scanner’s log file at /var/log/policy/scanner.log
[master@cli] $ cd /etc/Kubernetes/config
1. Edit kubeconfig to explicity deny
[master@cli] $ vim kubeconfig.json
“defaultAllow”: false # Change to false
2. fix server parameter by taking its value from ~/.kube/config
[master@cli] $cat /etc/kubernetes/config/kubeconfig.yaml | grep server
server:
3. Enable ImagePolicyWebhook
[master@cli] $ vim /etc/kubernetes/manifests/kube-apiserver.yaml
– –enable-admission-plugins=NodeRestriction,ImagePolicyWebhook # Add this
– –admission-control-config-file=/etc/kubernetes/config/kubeconfig.json # Add this Explanation
[desk@cli] $ ssh master
[master@cli] $ cd /etc/Kubernetes/config
[master@cli] $ vim kubeconfig.json
{
“imagePolicy”: {
“kubeConfigFile”: “/etc/kubernetes/config/kubeconfig.yaml”,
“allowTTL”: 50,
“denyTTL”: 50,
“retryBackoff”: 500,
“defaultAllow”: true # Delete this
“defaultAllow”: false # Add this
}
}
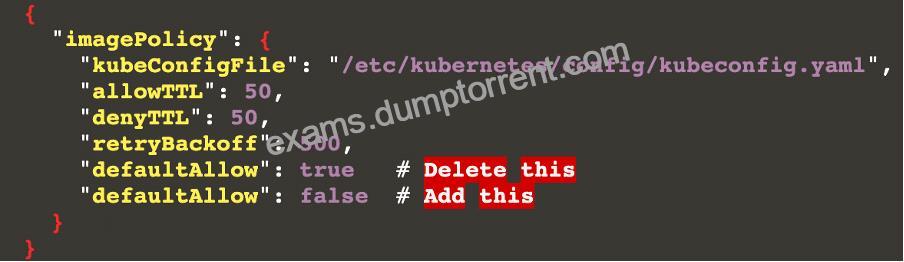
Note: We can see a missing value here, so how from where i can get this value
[master@cli] $cat ~/.kube/config | grep server
or
[master@cli] $cat /etc/kubernetes/manifests/kube-apiserver.yaml

[master@cli] $vim /etc/kubernetes/config/kubeconfig.yaml

[master@cli] $ vim /etc/kubernetes/manifests/kube-apiserver.yaml – –enable-admission-plugins=NodeRestriction # Delete This – –enable-admission-plugins=NodeRestriction,ImagePolicyWebhook # Add this – –admission-control-config-file=/etc/kubernetes/config/kubeconfig.json # Add this Reference: https://kubernetes.io/docs/reference/access-authn-authz/admission-controllers/
– –enable-admission-plugins=NodeRestriction # Delete This
– –enable-admission-plugins=NodeRestriction,ImagePolicyWebhook # Add this
– –admission-control-config-file=/etc/kubernetes/config/kubeconfig.json # Add this
[master@cli] $ vim /etc/kubernetes/manifests/kube-apiserver.yaml – –enable-admission-plugins=NodeRestriction # Delete This – –enable-admission-plugins=NodeRestriction,ImagePolicyWebhook # Add this – –admission-control-config-file=/etc/kubernetes/config/kubeconfig.json # Add this Reference: https://kubernetes.io/docs/reference/access-authn-authz/admission-controllers/